Share this
8 Security Steps To Protect Your MagicINFO Server From Hackers

MagicInfo is a digital signage solution by Samsung that allows users to play multimedia content on Samsung display devices. However, like any other server-based software, it can be vulnerable to security threats if not properly managed and secured.
Imagine if your screens suddenly displayed offensive messages or images that you clearly did not approve of. Your business's reputation could take a serious hit, leading to lost sales, upset customers and legal headaches. All because a hacker or a competitor decided to have some “fun”.
But here's the good news. There are steps you can take to prevent cyber attacks from gaining access to your MagicINFO server and causing mischief.
Important: If you suspect that your MagicINFO system has been behaving oddly recently or you suspect a security breach, contact us immediately to prevent unauthorised access and potential data loss!
What are the Common MagicINFO Server Security Threats?

Let's explore these security threats to digital signage systems and learn how cyber attackers use them and the damage they can cause.
1. Malware Attacks
Malware, short for malicious software, encompasses various types of harmful programmes, including viruses, worms, trojans and ransomware. It is designed to infiltrate, damage or take control of a system without the user's consent.
Attackers can spread malicious software through infected email attachments, compromised websites or corrupted USB drives. Once inside the digital signage system, it can execute a range of malevolent activities.
Malware can disrupt the normal functioning of digital signage, steal sensitive information stored on the system, or gain control over the screens. This can lead to displaying inappropriate content, loss of data or even extortion attempts through ransomware.
2. Hacking Attempts
Hacking attempts involve unauthorised access to digital signage systems by exploiting vulnerabilities or using stolen credentials.
Hackers might gain access to these systems to show offensive content, steal sensitive customer or business data. They might also embed malicious links within the signage content that can lead to further breaches or ransomware attacks when interacted with.
Hacking not only results in the immediate impact of inappropriate content being displayed but can also lead to significant data breaches. These breaches can undermine customer trust, result in legal issues and lead to financial losses due to the theft of intellectual property or customer information.
3. Social Engineering Attacks (Phishing)
Social engineering attacks, particularly phishing, involve deceiving individuals into providing sensitive information such as login credentials or financial information.
These attacks often use seemingly legitimate emails or messages that urge the recipient to perform an immediate action.
By tricking users of digital signage systems into sharing login credentials, attackers can gain unauthorised access to the system. They may impersonate legitimate sources, such as software providers or IT support, to convince users to provide access.
After gaining access, attackers can engage in various malicious activities such as stealing sensitive information, installing malware, or misusing the digital signage system to spread misinformation or malicious content. These actions have the potential to damage the organisation's reputation and result in financial losses.
If attackers breach the Windows server of the digital signage system, they could access a wider array of sensitive company data, escalating the risk to operational security and potentially exposing confidential business information.
4. Unsecured Networks
An unsecured network is one that lacks proper security measures, such as encryption and strong password protection, making it vulnerable to unauthorised access and attacks.
The use of unsecured networks can lead to data breaches, leading to the theft of sensitive information. Additionally, it can make organisations vulnerable to man-in-the-middle attacks, where data is intercepted and potentially altered. This compromises the confidentiality and integrity of the information displayed and transmitted by the digital signage system.
5. Man-in-the-Middle Attacks
In a man-in-the-middle (MitM) attack, an attacker intercepts the communication between two parties (e.g., between digital signage software and its content management system) without either party's knowledge.
Attackers can eavesdrop on or alter the transmitted data, such as intercepting passwords or modifying the content sent to digital signage displays.
MitM attacks can lead to information theft, including stealing personal or financial information. They can also result in the display of false or harmful content on screens, damaging the organisation's reputation and potentially leading to financial losses.
6. Denial-of-Service (DoS) Attacks
A DoS attack aims to make a system, network or website unavailable by overwhelming it with a flood of internet traffic or requests, exceeding its capacity to respond.
By targeting digital signage systems, attackers can overload the servers with requests, causing the system to slow down significantly or crash, rendering the digital signage inoperable.
DoS attacks can cause significant downtime for digital signage systems and disrupt communications and advertising campaigns. This can lead to lost revenue, decreased customer satisfaction and potential safety issues in environments where digital signage is used for critical information dissemination.
7. Network Eavesdropping
Network eavesdropping involves unauthorised listening to or monitoring of network traffic. This can be done to intercept and collect data being transmitted over the network.
Attackers can use eavesdropping to gather sensitive information transmitted by digital signage systems, such as login credentials, financial information or proprietary content.
The theft of sensitive information through network eavesdropping can lead to data breaches, financial losses and damage to the organisation's reputation. It can also compromise the privacy of individuals whose information is displayed or processed by the digital signage system.
8. Physical Tampering
Physical tampering involves direct, unauthorised physical interaction with digital signage devices, such as displays, media players or servers.
It can lead to the theft of hardware and data, unauthorised display of content and physical damage to the digital signage infrastructure. It can also result in financial losses due to the need for repairs, replacements and increased security measures.
How to Protect Your MagicINFO Server from Hackers

The following steps will help you implement the basic security measures to enhance your system's safety.
1. Update Your MagicINFO Software
One of the most essential things you can do to keep your system safe is to stay up-to-date with MagicINFO updates at all times.
Some of the old and outdated versions of MagicINFO have been identified as having significant security vulnerabilities. If you have one of these versions, it is essential to address these issues right away to remain safe.
The latest versions are V8 and V9, which can be downloaded for free from here, along with relevant installation guides.
2. Use Strong Authentication Measures
Securing your digital signage system is like ensuring your business's front door has a strong lock.
Start by setting tough-to-guess passwords that mix letters, numbers and symbols. For example, “F02mygo[O&],19hu” has lower and upper case letters, numbers and special symbols.
Remember to change the passwords regularly, for example, every month. To double-check who's trying to enter, employ multi-factor authentication (MFA), which requires both a password and a code sent to your phone—like needing two keys to open a door.
Additionally, it is important to control access permissions, similar to creating a guest list for a private event. This way, you give people only the access they need for their job, keeping your system secure and your business safe.
3. Set up MagicINFO Security Settings Correctly
You can set up basic protection for your devices through MagicINFO. Log into your MI server, navigate to Device and click on the Info (i) button on your device/s. Click Edit and then Security.
You will be presented with a few options that will allow you to protect your device:
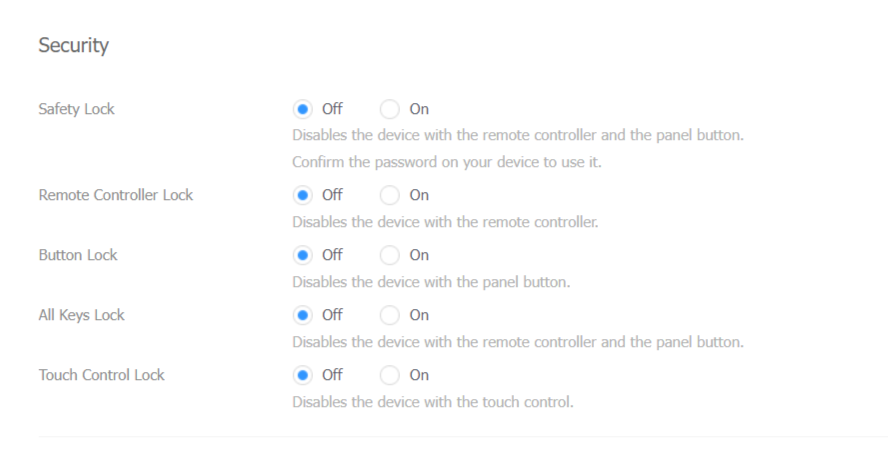
- Safely Lock - password-protects your remote control using a PIN code
- Remote Control - disables the remote control
- Button Lock - disables the usage of display buttons
- All Keys Lock - locks the display buttons and the remote control
- Lock Touch Controls - disables your display’s touch-screen functionality
Premium users also have a few additional advanced security settings:
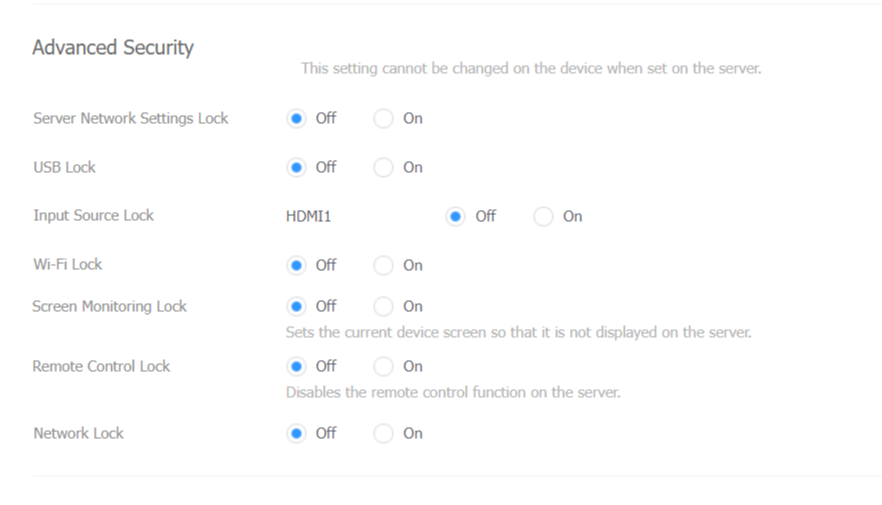
- Server Network Settings Lock - Locks the server network
settings in the screen menu - USB Lock - disables USB ports on the device
- Input Source Lock - locks the connection input source
- Wi-Fi Lock - locks the Wi-Fi settings
- Screen Monitoring Lock - disables the remote preview function from
MagicINFO - Remote Control Lock - disables server remote control function
- Network Lock - locks the network settings
4. Secure Your Network Connections
Using a VPN, or Virtual Private Network, is like sending your digital signage system's information through a private tunnel when you access it from somewhere else. This private tunnel keeps your information safe and hidden from anyone trying to peek in, making sure only you can see it.
When connecting your digital signage system to Wi-Fi, using WPA3 encryption ensures your network is well-protected. Also, hiding your Wi-Fi name (SSID broadcasts) keeps it off the radar from those you do not want connecting.
It is wise to change your Wi-Fi password often to maintain security. Avoid using public or guest networks for your digital signs. They are much safer on a dedicated, secure Wi-Fi connection designed specifically for them.
5. Install an SSL Certificate on Your MagicINFO Server
Secure your MagicINFO server's communication by adding an SSL certificate. This step encrypts data between your server and its users and ensures that information like passwords and personal details are transmitted safely.
Once installed, configure your MagicINFO settings to use HTTPS. Regularly check the certificate's expiration date to renew it on time and maintain uninterrupted protection.
6. Backup Your Data Often
Backing up your digital signage system's data involves regularly saving this information in different locations, such as online (in a cloud) and physical drives, to protect against data loss.
7. Perform Regular Security Audits and Risk Assessments
Regular security audits and risk assessments help in uncovering and addressing vulnerabilities within your digital signage system.
To ensure a thorough examination, schedule these audits every six months and after any major system updates or additions.
Involving external security experts could offer a fresh perspective, uncovering potential weaknesses that might go unnoticed by the internal team.
8. Train Your Employees
Teaching your team about security helps keep your digital signs safe. Offer lessons on online safety, recognising scams and handling important information to minimise security risks.
Why Professional Help Is Your Best Defence
If you are looking for a secure, all-in-one solution for your digital signage needs, opting for a MagicINFO Cloud service may be your best course of action.
This cloud-based solution is closely managed by MagicINFO professionals with 10+ years of experience, who are also official partners with Samsung.
Opting for the cloud solution grants you access to top-tier, proven security measures and regular updates, along with the expertise of experienced professionals. This can be achieved without the need for extensive in-house technical knowledge.
Focus on running your business without worrying about your signs getting hacked.
Share this
- Signage strategy (72)
- Content management (51)
- Solutions (44)
- Content creation (41)
- Device management (31)
- Content automation (29)
- Hardware (28)
- Getting started (27)
- Server management (25)
- MagicINFO Explained (23)
- Software (18)
- Security (14)
- Blog Post (12)
- Content design (9)
- Company and services (8)
- User management (6)
- Innovations in digital signage (5)
- Data management (4)
- Digital Signage Strategy (3)
- MagicINFO Cloud (3)
- Government (2)
- LATEST (2)
- AI (1)
- Consumer Experience in retail (1)
- Content Starting Package (1)
- Digital Signage in Retail (1)
- ISE (1)
- LOOKBEYOND Topics (1)
- Sustainability (1)
- februari 2026 (1)
- januari 2026 (1)
- november 2025 (1)
- oktober 2025 (1)
- juni 2025 (2)
- mei 2025 (3)
- april 2025 (2)
- maart 2025 (1)
- februari 2025 (4)
- januari 2025 (1)
- november 2024 (1)
- oktober 2024 (2)
- september 2024 (1)
- augustus 2024 (2)
- juli 2024 (3)
- juni 2024 (3)
- mei 2024 (6)
- april 2024 (4)
- maart 2024 (5)
- februari 2024 (3)
- januari 2024 (4)
- december 2023 (4)
- november 2023 (4)
- oktober 2023 (5)
- september 2023 (3)
- juli 2023 (5)
- juni 2023 (8)
- mei 2023 (9)
- april 2023 (8)
- maart 2023 (9)
- februari 2023 (7)
- januari 2023 (8)
- december 2022 (5)
- november 2022 (7)
- oktober 2022 (9)
- september 2022 (6)
- augustus 2022 (8)
- juli 2022 (6)
- juni 2022 (6)
- mei 2022 (7)
- april 2022 (2)
- maart 2022 (3)
- februari 2022 (1)
- januari 2022 (4)
- december 2021 (2)
- november 2021 (4)
- oktober 2021 (4)
- september 2021 (6)
- augustus 2021 (3)
- juli 2021 (6)
- juni 2021 (3)
- mei 2021 (3)
- april 2021 (3)
- maart 2021 (4)
- februari 2021 (3)
- januari 2021 (3)
- december 2020 (4)
- november 2020 (3)
- oktober 2020 (2)
- september 2020 (3)
- augustus 2020 (2)
- juli 2020 (3)
- juni 2020 (3)
- mei 2020 (1)
- april 2020 (4)
- maart 2020 (3)
- februari 2020 (2)
- januari 2020 (3)
- december 2019 (2)
- oktober 2019 (2)
- september 2019 (1)
- juni 2019 (3)
- mei 2019 (1)
- april 2019 (1)
- maart 2019 (3)

No Comments Yet
Let us know what you think